WannaCry Ransomware is the new malware that has highly spread to most countries around the world.
What is Ransomware Malware?
To achieve that, they have to incentivize the user to download or to choose the malware by mistake.
However, the process is gradual and encrypts all files one after the other.
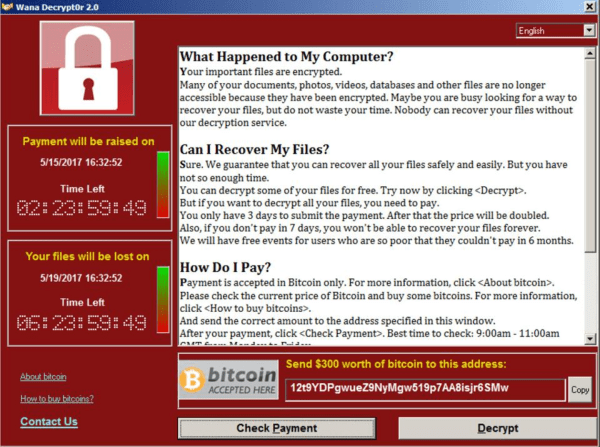
The criminals will demand varying ransoms.
In the year 2014, victims in the UK had to pay $700 to access their files again.
However, the criminals do not guarantee access to files after the ransom payment.
After that, they demand hundreds in cryptocurrency form for the download to start.
Microsoft announced the vulnerability earlier in March advising users to start patching their devices.
Microsoft managed to fix the MS17-010 in the March release.
However, it is likely that the affected organizations had not patched their computer devices before the malware spread.
The MS17-010, commonly known as the EternalBlue is linked to the Shadow brokers group.
How the Wanna Decryptor Spread?
The WannaCry is now advanced.
Worm-like fashions may also arise because the ransomware actors are now in the retooling stage.
Main cause of spread are clicking on the suspicious links or downloading suspicious documents from the mails.
Those mails look legitimate and confused the user to made them to punch the malware.
They trick the users to get the permission to enter into the system.
So Antivirus are not the full proof protection for this punch in of crypto malware or Ransomware.
Use the multiple layer of protection to keep your rig safe from cyber attacks.
However, individuals are not lucky enough and can lose access to their information at the end.
In fact, cyber criminals demand payments in return for files unlock.
The payments are mostly in the form of online crypto currency such as Bitcoin.
Do not expect lawmakers to help you fight ransomware attacks.
That way, you will end up paying many ransoms, as most victims have done.
In 2016 alone, Americans lost over $24 million to cyber-criminals.
Including if you have backed up your data in the safe places, the attack may still cost you.
They incurred machines disinfection costs and backup data restoration, which took days or weeks.
The cost will highly depend on the organization.
The following are a few things to do.
Companies have lost thousands of files in a single attack.
With backup, it’s possible for you to always retrieve your data.
That is also true for people who use external hard drives to do their machine backups.
Connect the drives when doing a backup and then disconnect it.
If your backup is connected at the particular time the malware runs, it might also be encrypted.
Data backups will not make the attack painless because your business operations might stop for days or even weeks.
Hospitals have paid the ransom amounts to save lives.
The attack involves spamming users with emails that feature malicious attachments.
The emails may also instruct users to press URLs to allow the malware to crawl surreptitiously into the machine.
Patch any known internet tool security hole to thwart malvertising.
Patch and block
As a user, you are not the stopgap for infections.
Many available systems use deeper learning to detect malware like ransomware and block them.
However, security products are fallible.
Otherwise, businesses and individuals would not be a target of many ransomware and other malware.
Companies should apply other standardized security measures to protect their data.
The methods include patching software program security holes to prevent exploitation from malicious systems and infections on their systems.
Another option is to use whistling software because the lists will not allow installation of unapproved software.
Administrators can also employ segmentation access to prevent critical data access with redundant servers.
The tactic can also force attackers to situate and lock down the other servers to make an assault effective.
After that, the victim should venture to determine the throw in of ransomware malware that affected them.
In the traditional hacks, the level of pain is low and victims are able to move on.
However, ransomware can bring your businesss operation to a standstill.
In case of individuals, accessing family photos and the other personal files becomes impossible after an infection.
The level of pain associated with that is high.
We can stop fueling the engine that is driving the ransomware attacks by not paying.
However, that depends on the expected loss.
That means hospitals, banks, police departments, Congress, airport, and airlines should remain vigilant.
Large corporations and government agencies are also at a threat.
The other attack is home computers.
However removal of the infection (without recovering data) is possible by scanning with malware scanners.
We will update you as soon as we get any update regarding WannaCry Ransomware.
Before starting process of removing WannaCry from computer, read the below instructions carefully.