What is VPN?
A VPN, which means Virtual Private web link in full, is a technology used in networking.
Virtual Private Networks may give employees a secure access to a corporate intranet while located outside the office.
They are used in securely connecting other offices of an organization that exists in other geographical locations.
It creates a cohesive internet.
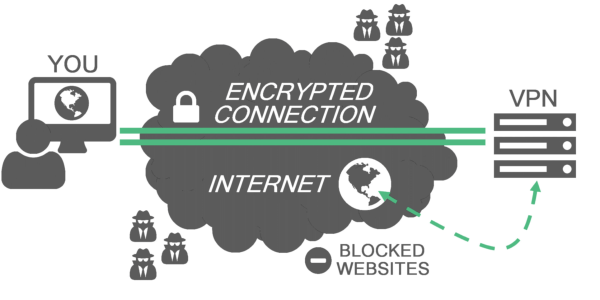
Individual Internet users may also use VPN services for securing their wireless transactions, escape censorship and geo-restrictions.

VPN also used for proxy servers connection for the purpose of protecting location and personal identity.
However, some websites obstruct access to known VPN technologies to disallow them from circumventing geo-restrictions.
Why Use VPN Service?
Internet service providers can sell the browsing history of their customers to the highest bidders.
That also includes the internet service provider.
So after using a APN your ISP can not track your information.
Some people will interpret that as another problem.
The VPN might also start selling your information to the highest bidders.
Do not panic, yet.
Of course, there are many reputable VPN service providers out there.
As an internet user, you should properly do your homework.
The design of IPSec meets most security goals such as integrity, authentication, and confidentiality.
Internet Protocol Security uses encryption in the process of encapsulating the packet of an IP inside an IPSec packet.
These include:
This is used in securing communications over the Internet.
IPSec traffic can use either tunneling or transport mode in encrypting data traffic in a virtual private data pipe.
IPSec is often used as a security layer for other protocols.
These protocols utilize cryptography in securing communications over the Internet.
An authentication process involving certificates is used in successfully initiating a connection.
A certificate is a cryptographic key that is stored on both the client and server.
This is another protocol used in connecting a private server with a remote client over the Internet.
This is a protocol used in tunneling data traffic between two sites over the Internet.
However, implementing VPN using L2TP/IPSec requires the use of certificates or shared key.
It offers VPN tunneling to secure remote connections to inter-internet links or a internet.
The server of OpenSSH provides a limited number of simultaneous tunnels.
The virtual private web connection feature itself doesnt support personal authentication.
VPN technology employs advanced encryption to prevent any unintentional interception of data between private websites and ensure security.
All traffic over a virtual private online grid is encrypted using algorithms to secure privacy and data integrity.
They are likely to track your movements and activities online.
Therefore, you should only select a trustworthy VPN service provider.
Check whether the VPN will keep a log of your activities.
Most privacy-focused virtual private networks are intentionally upfront about no-log policies.
It is therefore important you check the terms of service.
They will help you understand the VPNs policy about when they can disclose your logging information.
You have to understand that even VPNs are not foolproof.
Companies can misrepresent their logging practices or accidentally store their data for longer periods than necessary.
List of best & reputed VPN service providers