For your rig to communicate with any other rig it needs to connect to it.
If the other unit is physically present, this is pretty simple.
you could just run a cable between the two devices.
It is necessary for them to share some sort of communication standard but the basic principle stands.
Of course, most of the devices you might want to communicate with are not physically present.
Instead, you oughta connect to them over a computer internet typically with the Internet involved.
To communicate properly through intermediary parties, you’re gonna wanna be able to trust them.
Alternatively, it’s crucial that you be able to ensure that they cant read or modify your communications.
This is the basis of encryption.
It allows you to communicate securely over an insecure channel.
One way they can attempt to do that is to perform a Man-in-the-Middle attack or MitM.
There are a few ways to achieve this.
Theoretically, anyones ISP could also target them as their traffic runs through their ISP.
As such all of the same security concerns should apply to them too.
Still, encryption protects from those that are and helps to improve your privacy.
An attacker in a MitM position may simply use their position to listen to the traffic flow.
In this way they can track some vague details of encrypted traffic and can read unencrypted traffic.
In this sort of scenario, an attacker in a MitM position can always read or modify unencrypted traffic.
It is only encryption that prevents this.
As such, they may attempt to perform an active attack instead.
In this scenario, they fully insert themselves in the middle of the connection acting as an active middleman.
They negotiate a secure connection with the server and attempt to do the same with the end user.
This is where things typically fall apart.
Each HTTPS website serves an HTTPS certificate.
Root certificates are special because they are stored in the trusted certificate store of every unit.
The post office and system are like the Internet but for sending letters.
The person that delivers your post, however, is in a perfect Man-in-the-Middle position.
They could choose to open any letter before they deliver it.
In this scenario, youre actually never really communicating with the person you think you are.
Instead, both of you are communicating with the nosy post person.
If you start communicating via email, the post person cant read or modify your messages anymore.
Conclusion
MitM stands for Man-in-the-Middle.
It represents a situation where a messenger in the chain of communication is maliciously monitoring and potentially editing communications.
Typically, the most risk is from the first hop, i.e.
the router you connect to.
A free Wi-Fi hotspot is the perfect example of this.
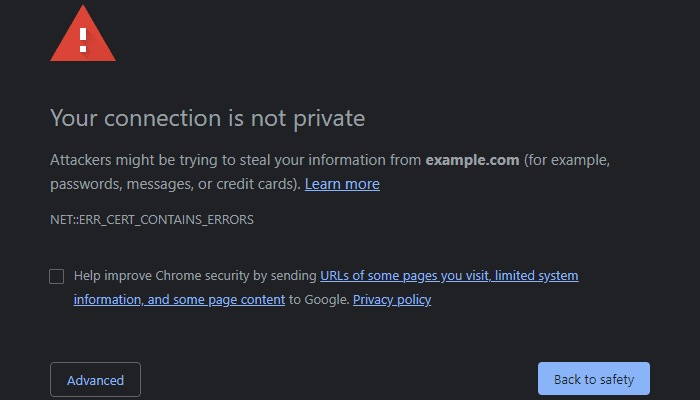
An attacker in a MitM position can read and edit unencrypted communications.
They can also try the same with encrypted communications but this should result in certificate validation error messages.
This works because both parties communicate with the attacker rather than actually with each other.
The attacker poses as the other party to both parties.