To gain access to many computer systems, it’s crucial that you authenticate yourself.
Authentication is the process of proving your identity.
In computing, this is typically done in two parts.
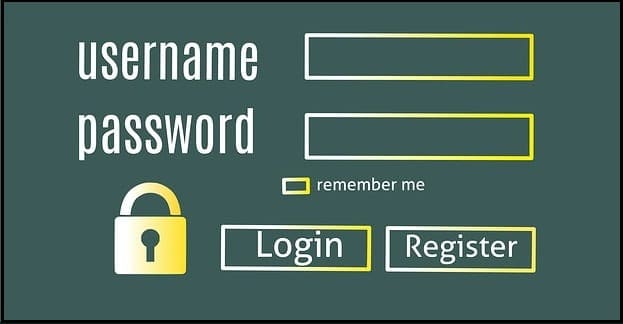
The first is alleging your identity; the second is providing some evidence.
The classic example is using a username to allege your identity and then providing a password to prove it.
Another form of authentication could be a challenge-response interaction.
Contents
Usefulness in the Modern World
Authentication is critical to the function of the modern digital world.
The first form of authentication is to your unit.
Without this step, anyone could access any machine they had physical access to.
Authentication is doubly important when signing into an online service.
The most obvious instance is you proving your identity to the website.
This allows you to sign into your account and prevents other people from accessing it.
Authentication is also essential in verifying that youre connecting to the website you think you are.
HTTPS and other encrypted connections utilize a certificate system to authenticate the website to the user.
It only verifies that the connection to the typed website is secure from snooping.
Malware, phishing, and spam can all be served with legitimate certificates.
This relies on the secrecy of something you know, your password.
It also leaves you open to being tricked into giving it away.
A common method for this to happen is phishing.
Depending on your chosen password, it may also be possible to guess.
Another form of authentication involves the use of a physical token.
This punch in of authentication relies on something you have.
However, it has big consequences if your physical token is lost or stolen.
This is why many RFID access badges are unbranded and plain.
It means a thief cant immediately know which building they can access.
The final field of authentication is biometrics.
This involves verifying something about your person.
Biometric authentication techniques are excellent ways to verify identities but have some problems.
For one thing, many of these features are somewhat public.
Another particular issue is that you cant change biometric features if they are compromised.
Once your fingerprints are public, anyone can use them.
Conversely, an accident could change a range of biometric features, locking you out of your account.
Two-Factor Authentication of 2FA uses the above techniques to authenticate your identity.
MFA or Multi-Factor Authentication is the same but may extend to more than two factors.
For example, a hacker with your password usually wont have access to your smartphones authenticator app.
Conversely, a thief with your smartphone might have your authenticator app but doesnt have your password.
Biometric attacks generally cause you to be specifically targeted.
The other types of attacks are typically opportunistic.
An attacker dedicated enough to target you and your biometric details is likely capable of performing different attacks too.
Conclusion
Authentication is the process of verifying identity.
Secret passwords are a standard form of authentication, though certificates and challenge-response processes also work based on knowledge.
Biometrics will enable you to be identified by your features.