A user interaction is any action that involves the website processing a form of user action.
Intruder is designed to be a tool to automate the testing of any potential vulnerability source.
The sent requests will then be visible in the Intruder tab.

Ensure you have permission from the website owner before trying this.
How to use Intruder
You generally dont need to configure the Target sub-tab in the Intruder tab.
The Target tab is used to configure the host being attacked.
The Positions sub-tab is used to select where in the request you want to insert payloads.
To dump the selected insertion points, click Clear on the right-hand side.
To add insertion points, highlight the area you want to be changed, then click Add .

The attack throw in dropdown box is used to determine how payloads are delivered.
Sniper uses a single payload list and targets each insertion point one by one.
Battering ram uses a single payload list but inserts the payload in all insertion points at once.
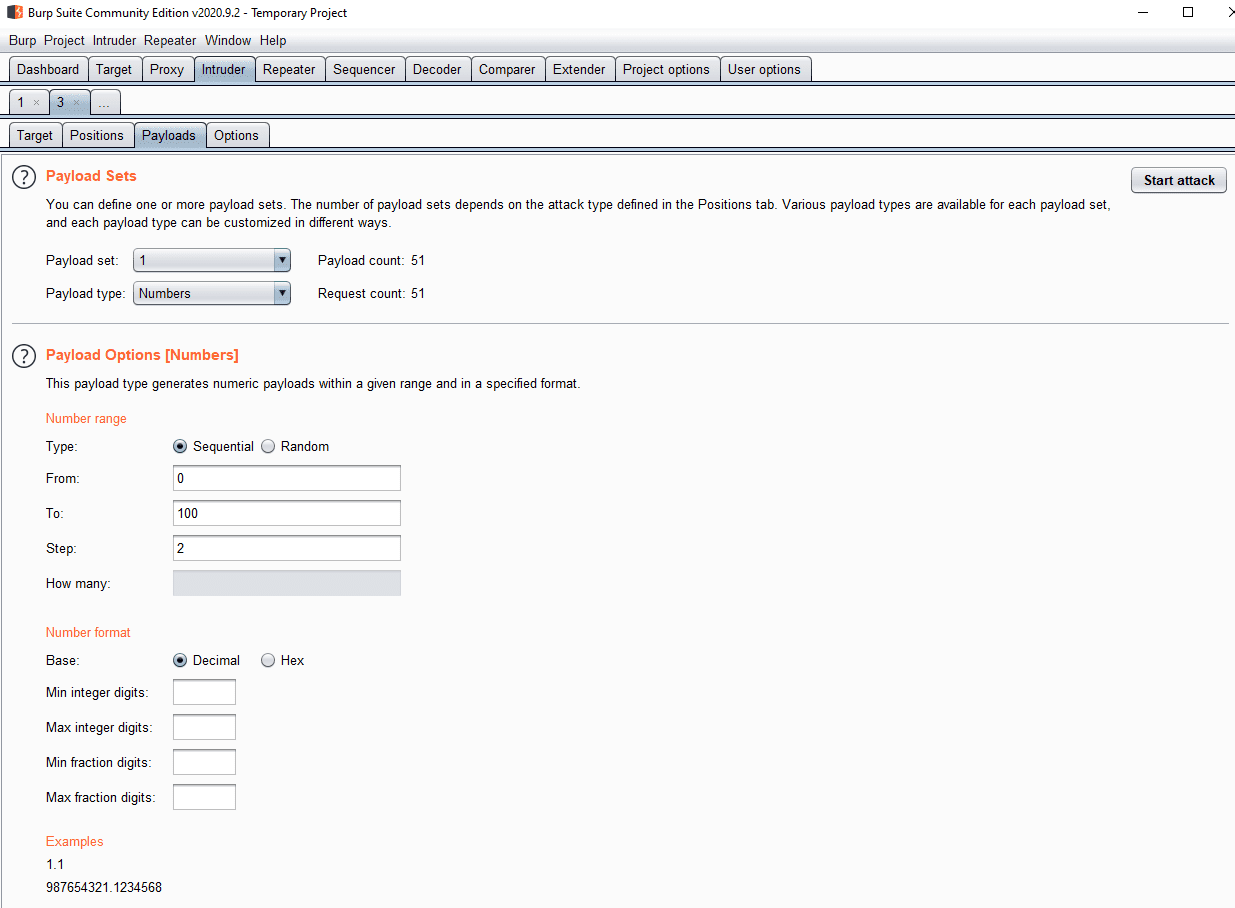
The Payloads sub-tab is used to configure the payloads that are attempted.
The payload key in is used to configure how you specify the payloads.
Payload processing allows you to modify the payloads as theyre being submitted.

The payloads tab is used to configure the payloads to be inserted in the insertion points.
The Options sub-tab allows you to configure a number of background options for the scanner.
you could add grep-based result matching systems designed to help you identify key information from meaningful results.
By default, Intruder doesnt follow redirections, this can be enabled at the bottom of the sub-tab.
The Options tab allows you to configure some extra background options but can generally be left alone.