The primary purpose of Burp Suite is to intercept and modify web traffic as part of a penetration test.
Tip: To be operational the proxy listener must have the running checkbox on the left ticked.
Select a listener then click edit or add a new one.

Binding to the loopback address means that the proxy is only available to the local computer.
Selecting All interfaces will make the proxy visible on all of the IP addresses your gear has.
Remember that youll have to load the Burp certificate on those devices to monitor their HTTPS traffic.

The Binding tab allows you to set the IP address and port number used by the proxy.
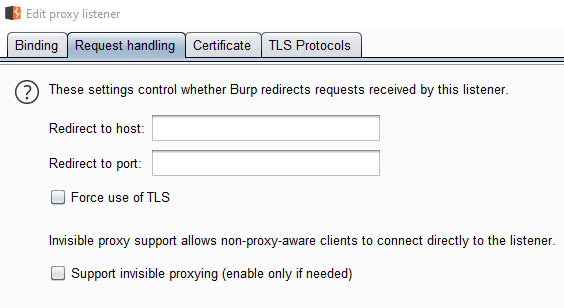
This option is used to forward traffic through another proxy.
Force TLS automatically upgrades all web requests to use HTTPS.
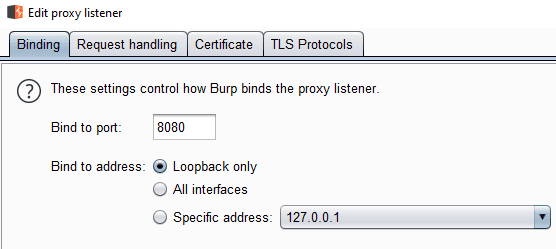
This option can break some websites if they dont support HTTPS.
Invisible proxying enables support for devices that dont support traditional proxy tweaks.
The Request handling tab allows burp to work with other proxies.
The Certificate tab allows you to configure how the HTTPS certificate works.
Generate CA-signed per-host certificates is the default setting and should generally be used.
Self-signed certificates will always generate certificate error messages.

Specifying a specific hostname is only useful when performing invisible proxying to a single domain.
If a specific certificate is required, you might import it with the custom certificate option.
The Certificate tab is used to configure which certificate is presented.
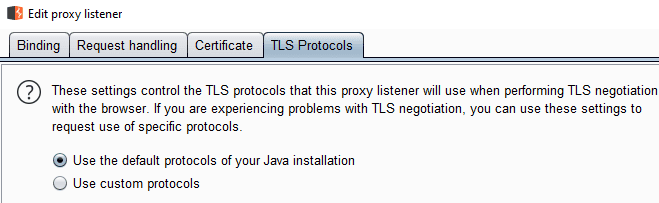
The TLS Protocols tab allows you to specify which TLS protocols you want Burp to support.
By default, TLSv1-1.3 is supported.
The TLS Protocols tab is used to configure which TLS protocols Burp can use to connect.