Running a port scan can give you an accurate overview of the attack surface of your system and internet.
In some cases, you may find that you have services running that you may not have expected.
Transmission Control Protocol, or TCP, is a standard that allows connections between computers over a connection.
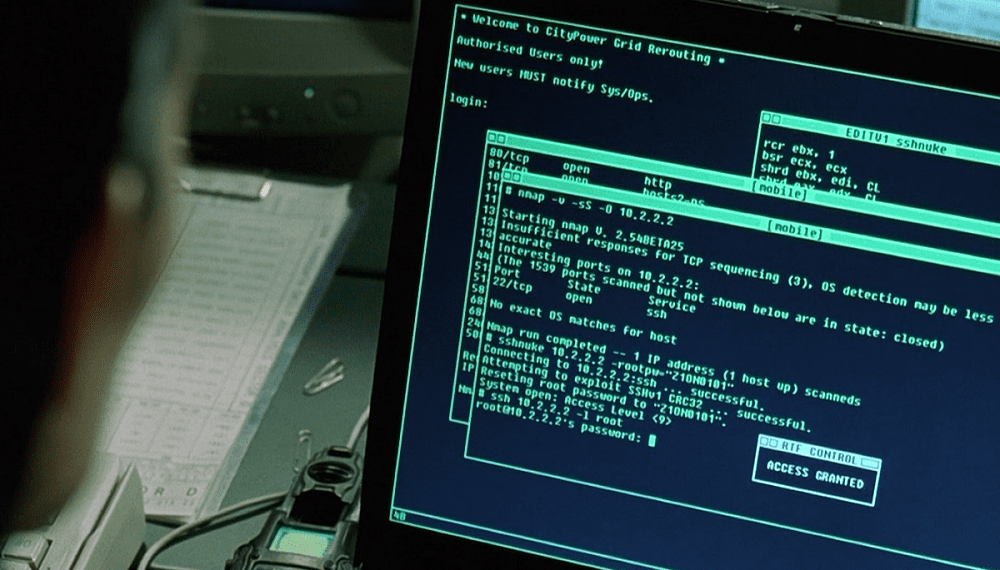
Nmap is the standard tool for performing port scanning.
Its designed primarily to run on Linux but there are also Windows versions.
A graphical interface is also available, but the command-line usage is still the standard.
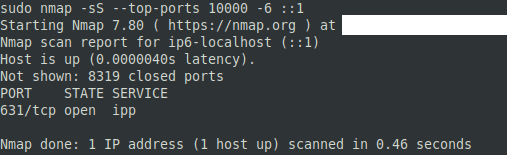
The help page is very dense and shows a lot of options that can be confusing.
The basics that you’re gonna wanna scan TCP ports are relatively simple.
For scanning TCP ports youll want to use one of two scan types, TCP or SYN.
A TCP scan attempts to make a full connection to each port, completing the three-way handshake.
A SYN scan abuses the protocol slightly and never sends the third message of the three-way handshake.
A TCP scan is specified with the -sT flag, while a SYN scan is specified by -sS.
If you specify a large range it can take a long time to scan.
Port ranges can be specified through comma-separated-values, hyphenated ranges, or a combination of the two.
If you want to specify all ports, you’re free to use the shorthand -p-.
Tip: Port numbers range between 0 and 65535, although 0 technically cant be used.
The last thing you should probably specify is the IP addresses of the devices you wish to test.